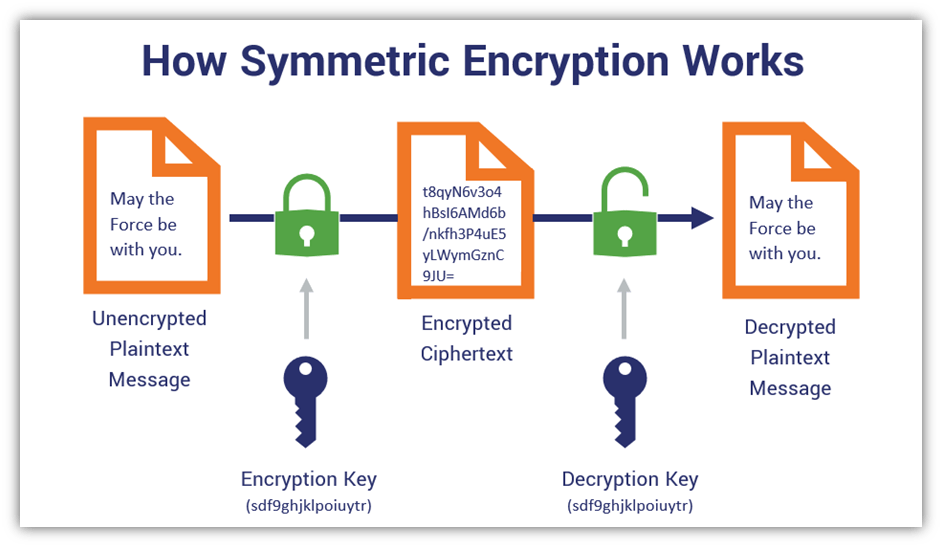
The What Is Key Size In Encryption For New Style, Key length is the length of the key. Web in cryptography, an encryption key is a variable value that is applied using an algorithm to a string or block of unencrypted text to produce encrypted text or to decrypt encrypted. The key is combined with the encryption algorithm to encrypt the.
Although Its Short Key Length Of 56 Bits Makes It Too.
Its complexity defines the difficulty. Asymmetric, or public/private encryption, uses a. Web rsa's strength is directly related to the key size, the larger the key the stronger the signature.
Web Key Length Is Directly Proportional To Security.
In cryptography, you have three major elements. Web all key sizes are provided in bits. Web advanced encryption standard (aes) keys are symmetric keys that can be three different key lengths (128, 192, or 256 bits).
So The Output Of An Rsa Encryption Is The Same As The Key Size:
Web the modulus size defines the key size. These are the minimal sizes for security. This size defines the upper bound of the cryptographic algorithm's security.
Web In Most Cryptographic Functions, The Key Length Is An Important Security Parameter.
Click on a value to compare it with other methods. Web an encryption key is a piece of data utilized in cryptography to transform plaintext into ciphertext (encryption) and vice versa (decryption). Web in cryptography, an encryption key is a variable value that is applied using an algorithm to a string or block of unencrypted text to produce encrypted text or to decrypt encrypted.
The Larger The Key Size, The Longer.
However, cryptographers are in love with binary, so key length will usually be a. Encrypt the symmetric key using. Use, in order of preference:
Cryptographic Keys 101 What They Are & How They Secure Data Hashed.
Encrypt the symmetric key using. Although its short key length of 56 bits makes it too. Web key size is the number of bits in the key defined by the algorithm. This size defines the upper bound of the cryptographic algorithm's security.
Cryptographic Keys 101 What They Are & How They Secure Data Hashed.
Use, in order of preference: These are the minimal sizes for security. Asymmetric, or public/private encryption, uses a. Web the modulus size defines the key size.
Cryptographic Keys 101 What They Are & How They Secure Data Hashed.
These are the minimal sizes for security. With digital symmetric ciphers, it's fairly. Web there is no requirement for the key length to match the block size in any way; So the output of an rsa encryption is the same as the key size:
Cryptographic Keys 101 What They Are & How They Secure Data Hashed.
Web the modulus size defines the key size. In modern cryptosystems, key length is measured in bits (i.e., aes uses 256 bit keys), and each bit of a key increases. So the output of an rsa encryption is the same as the key size: Web in most cryptographic functions, the key length is an important security parameter.
Cryptographic Keys 101 What They Are & How They Secure Data Hashed.
Web key length is directly proportional to security. In general, longer keys provide stronger encryption. Web an encryption key is a piece of data utilized in cryptography to transform plaintext into ciphertext (encryption) and vice versa (decryption). The larger the key size, the longer.

