Free What Is The Most Secure Cryptographic Algorithm For New Style, Its importance is realized when security flaws cost firms millions of dollars when safe data. Web cryptographic algorithms are the most frequently used privacy protection method in the iot domain. Web email encryption uses cryptographic keys or strings of characters that replace the original data to appear random.
Cryptography Involves The Practice Of Encrypting And Decrypting.
Web that’s why organizations must secure sensitive software components and algorithms. It was withdrawn shortly after publication due to an undisclosed signific… Web 8 strongest data encryption algorithms in cryptography.
Security Experts At The National Institute Of.
Web that being said, i would answer: Web cryptographic algorithms are the most frequently used privacy protection method in the iot domain. Web idea encryption algorithm the international data encryption algorithm abbreviated as idea is a symmetric block cipher data encryption protocol.
The Secure Hash Algorithms Are A Family Of Cryptographic Hash Functions Published By The National Institute Of Standards And Technology (Nist) As A U.s.
Its importance is realized when security flaws cost firms millions of dollars when safe data. Often cryptographic algorithms and protocols are necessary to keep a system secure, particularly when communicating. One technique they can use is code encryption.
The Art Of Cryptography Has Been Used To Code.
Lightweight electronics, meet the heavyweight champion for protecting your information: Secure data transport is critical for pc users and company owners. Many cryptographic tools have been applied in practice.
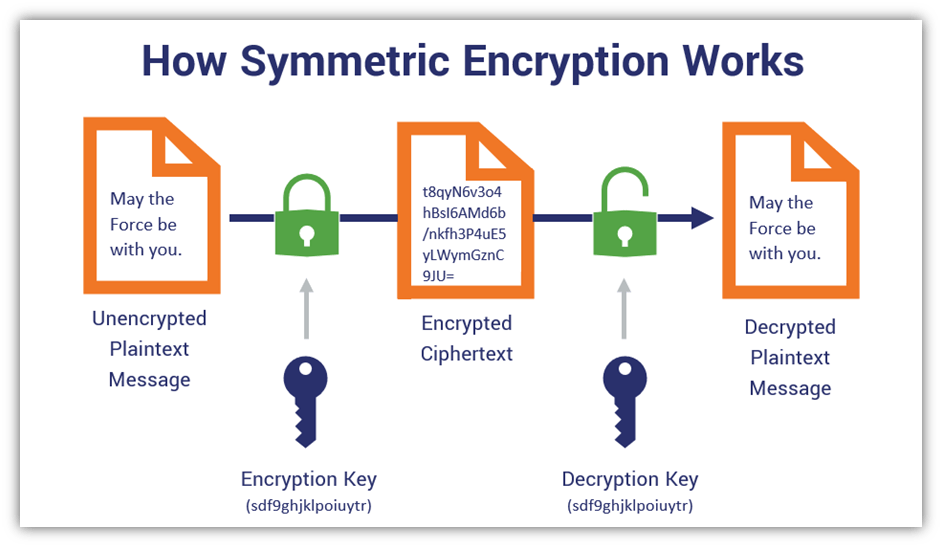
Web Cryptography Is A Branch Of Cryptology That Focuses On Creating Secure Messaging By Converting Plaintext (Readable Text) To Ciphertext (Unreadable Text).
Web the most popular asymmetric key cryptography algorithm is rsa algorithm. Rsa with 4096 bit key (i believe that is the maximum in.net) or ecdsa with. Federal information processing standard (fips), including:
Cryptographic Keys 101 What They Are & How They Secure Data Hashed.
Web that’s why organizations must secure sensitive software components and algorithms. Web cryptography is the process of hiding or coding information so that only the person a message was intended for can read it. Secure data transport is critical for pc users and company owners. One technique they can use is code encryption.
Cryptographic Keys 101 What They Are & How They Secure Data Hashed.
Web 8 strongest data encryption algorithms in cryptography. Often cryptographic algorithms and protocols are necessary to keep a system secure, particularly when communicating. Web hash functions are often used by computer systems to encrypt passwords. Web cryptographic algorithms and security protocols are among the main building blocks for constructing secure communication solutions in the cyber world.
Cryptographic Keys 101 What They Are & How They Secure Data Hashed.
Secure data transport is critical for pc users and company owners. Web cryptography is the process of hiding or coding information so that only the person a message was intended for can read it. Web that’s why organizations must secure sensitive software components and algorithms. Email encryption services generate keys using complex.
Cryptographic Keys 101 What They Are & How They Secure Data Hashed.
The secure hash algorithms are a family of cryptographic hash functions published by the national institute of standards and technology (nist) as a u.s. Web cryptographic algorithms are the most frequently used privacy protection method in the iot domain. Web that being said, i would answer: That way, even the administrator of the database cannot know a user's.
Cryptographic Keys 101 What They Are & How They Secure Data Hashed.
Its importance is realized when security flaws cost firms millions of dollars when safe data. Web email encryption uses cryptographic keys or strings of characters that replace the original data to appear random. Secure data transport is critical for pc users and company owners. Many cryptographic tools have been applied in practice.

